Samba Settings
This screen displays the configuration settings of the Samba server. The function of each field in the screen is explained below:
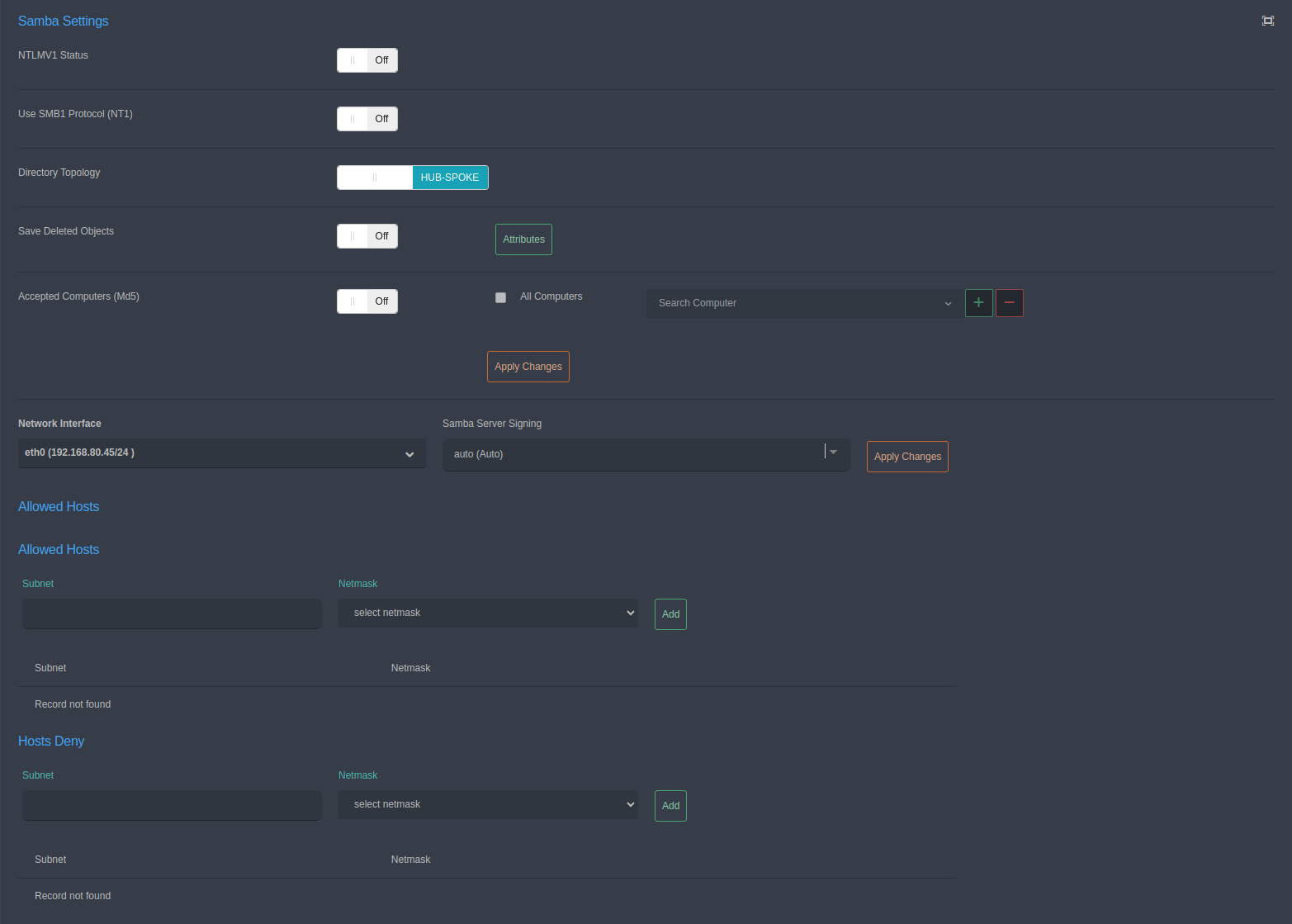
NTLMv1 Status: - This option determines whether the NTLMv1 (NT LAN Manager v1) protocol will be used. It is set to “Disabled”.
Use SMB1 Protocol (NT): - This option determines whether the SMB1 (Server Message Block v1) protocol will be used. It is set to “Disabled”.
Directory Topology: - This option specifies how the directory structure will be organized. The “STAR” option is selected.
Note
Hub-Spoke Topology: In a hub-spoke topology, a central hub manages communication between connected devices (spokes). The hub receives all data and directs it to the appropriate spoke. If the hub fails, the entire network stops functioning. This topology is often used for larger and more complex network structures, with centralized management.
Star Topology: In a star topology, a central switch or hub establishes individual connections with each device. In this structure, each device is directly connected to the central device, and communication between two devices occurs via the central device. If the central device fails, the entire network is affected, but if a device fails, only that device’s connection is lost. This topology is typically used for smaller networks and is easily expandable.
Set Functional Level: - This option sets and applies the domain functional level. The year 2016 is selected.
Save Deleted Objects: - This option determines whether deleted objects will be saved. It is set to “Disabled”.
Password Hash: - This option selects the password hash algorithm to be used. “sha256” is selected. An alternative “sha512” option is also available.
Accepted Computer (MD5): - This option determines whether accepted computers will be verified with an MD5 hash. It is set to “Disabled”.
Network Interface: - This option selects the network interface to be used by the Samba server. “lan0 (192.168.0.10/24)” is selected.
Samba Server Signing: - This option selects whether server signing will be done automatically or manually. “auto (Auto)” is selected.
Samba Client Signing: - This option selects whether client signing will be done automatically or manually. “auto (Auto)” is selected.
Allowed Computers (İzin Verilen Bilgisayarlar): - This option is used to list and add computers allowed to access the Samba server. The user can manually add allowed devices to the list by entering a specific Subnet, Netmask, IP Address, or Hostname. Currently, there are no records.
Denied Computers (Engellenen Bilgisayarlar): - This option is used to list and add computers that are denied access to the Samba server. The user can manually add devices to be restricted by entering a specific Subnet, Netmask, IP Address, or Hostname. Currently, there are no records.
These settings are used to manage the security and functionality of the Samba server and can be customized according to the needs of the system administrator.
Warning
Turning the SMB1 protocol on will cause security problems. NOT RECOMMENDED.
Note
What is SMB? SMB (Server Message Block) protocol; It is a protocol that transfers bulk data between networks in a secure and encrypted manner. We can usually see SMB data packets under the following headings;
Session Control Packages
File Access Packages
General Message Packages
SMB Versions? (SMBv1, SMBv2, SMBv3)
SMBv1 This protocol, created by IBM in the 1980s, can carry small data in 16-bit packets, well below today’s standards. SMBv1 does not have any encryption, making it insecure. However, today only peripherals (Printer, Scanner, etc.) that support the SMBv1 protocol are used.
SMBv2; It is a newer technology than SMBv1. The fact that it pulls data packets into 32-bit packets (or even 128-bit packets for file descriptors) is a significant improvement. In addition, performance improvement was achieved by reducing the number of subcommands from around 100 in SMBv1 to 20.
SMBv3; It includes security improvements such as strengthening secure connections with newer clients and stronger encryption protocols. SambaBox uses the SMBv3 protocol by default.
Warning
Turning the NTLMV1 protocol on will cause security issues and is NOT RECOMMENDED.
Note
What is NTLM (NT LAN Manager)? NTLMv1 and NTLMv2 are two different versions of NTLM authentication protocols with their own security levels.
NTLMv1 (NTLM version 1):
Security Level: NTLMv1 is considered less secure than NTLMv2.
Authentication Process: When a user logs in using NTLMv1, their password is hashed and sent over the network to the server or domain controller. The server also stores the password in an encrypted format. The server then verifies the user’s identity by comparing it with the encrypted data.
Weaknesses: NTLMv1 is vulnerable to certain attacks, such as a “pass-the-hash” attack. In this type of attack, the attacker can capture the hashed password and use it to gain unauthorized access.
Compatibility: NTLMv1 is still supported for backward compatibility with legacy systems, but NTLMv2 is recommended.
NTLMv2 (NTLM version 2):
Security Level: NTLMv2 is considered a more secure version than NTLM.
Authentication Process: NTLMv2 increases security by using a more complex encryption process and adding a time-based factor to the authentication process. It also requires the client and server to exchange challenge-response messages to verify identity.
Weaknesses: NTLMv2 is more secure than NTLM, but is still vulnerable to certain attacks, such as brute force attacks. However, it significantly reduces the risk compared to NTLM.
Compatibility: NTLMv2 is the recommended authentication protocol for directory solutions. It provides better security features and is less susceptible to attacks.
To summarize, NTLMv2 is a more secure and modern version of the NTLM authentication protocol. By including additional security measures, it is less vulnerable to various types of attacks than NTLMv1. It is recommended that you use NTLMv2 whenever possible to increase the security of your directory server network.